Yeah, they overlap since I did whole hour (120 30-second codes). I didn’t know specific time, so it’s 2 pages, 3 hours, 42 minutes and 30 seconds.
Credit goes to oathtool (and LibreOffice Write).
Font: Liberation Mono
Yeah, they overlap since I did whole hour (120 30-second codes). I didn’t know specific time, so it’s 2 pages, 3 hours, 42 minutes and 30 seconds.
Credit goes to oathtool (and LibreOffice Write).
Font: Liberation Mono
No.
Password I remember is the 1st factor, a valid code from this list (which depends on time) is the second factor.
It’s same as using the phone, except that here they were precomputed and on paper for some time span. None of these are valid now (well, maybe there is one, it’s a bunch of number combinations after all), and you don’t have the private key to generate more.
Say, you can tell that at 10:02:30 UTC the valid code was 262887, but you don’t know what it is now.
That’s the advantage of TOTP, they expire. If it were plain HOTP, I’d only need 1 code at a time anyway.
https://en.wikipedia.org/wiki/Time-based_one-time_password
It does. If you were to lose this paper while it were active any hacker could access your account. At least your phone has a PIN or pattern they also have to guess. This is just waiting there to be social engineered away from you (if it were still active, which good thing its not)
But they’d also need the password.
Alternative would be disabling 2FA altogether.
I believe most passwords are brute forced or phished nowadays, so unless you have some password manager changing your passwords every hour or so the password is probably pretty moot if the employee has to set it.
Brute-forcing would take some bit of time. If the 6 digit code, 3 combinations of which are likely valid at a time becomes your only factor, you’ve already lost. Long randomly generated combinations are unrealistic to brute-force. For now at least.
And here’s a screenshot from when I brute-forced the 2FA to my Lemmy account because I trusted the wrong app (Cisco Duo and its backups without version control wiping everything after turning on older device):
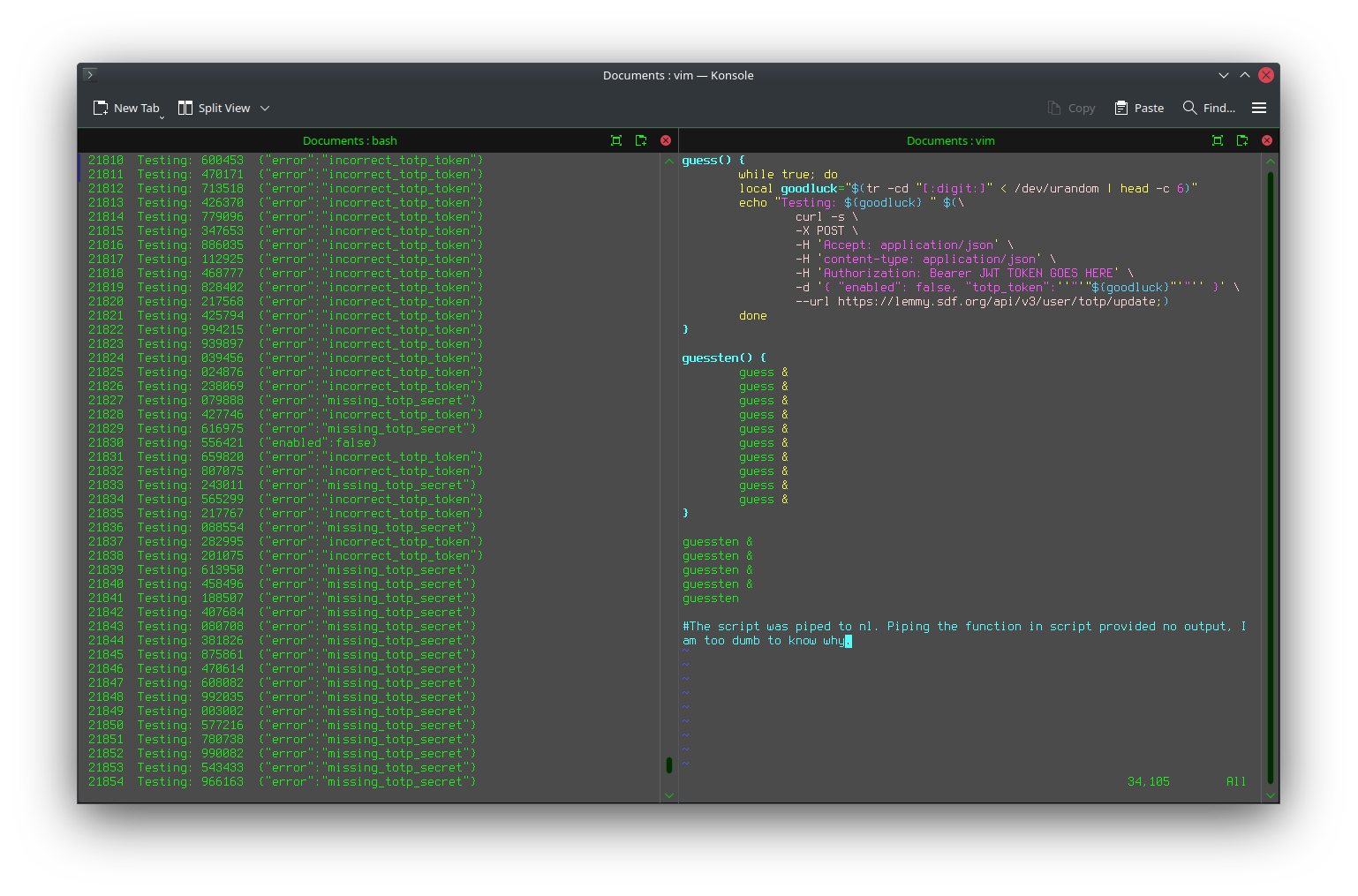 6 digits isn’t much.
6 digits isn’t much.
Also I hate how it’s implemented everywhere. We figured out that telling someone whether the password or username is incorrect is a bad thing, so now we do “username or password incorrect”. But what about 2FA? Username is easy to get if targeting a specific person.
If you can get to 2FA, you know the password was correct. That’s the case basically everywhere. Then it’s just 6 digits to guess. And typically you also only get notified about logins when successful. Too late at that point.
My wish would be to take both password and 2FA code at once, and just return “password or 2FA invalid” if one or both of them are wrong.
I wish hardware tokens or something were more prevalent or anything that doesn’t require me to visit 2 separate pages (login then 2fa) to login everytime. All the services I use at work timeout at ~15 minutes and it can be a slog. Software authenticators are convenient to keep track of but theres got to be a better way.
Any sane implementation should rate limit you to 3 tries/min