Yeah, they overlap since I did whole hour (120 30-second codes). I didn’t know specific time, so it’s 2 pages, 3 hours, 42 minutes and 30 seconds.
Credit goes to oathtool (and LibreOffice Write).
Font: Liberation Mono
One of the banks I’ve used actually had a bunch of codes printed on a scratch-to-reveal card, as a form of 2fa. Not time-limited, though, at least not per code. This was pretty long ago, even — around 2010.
grumbles I had to deal with this to access my timecard while i was working for a defense contractor, who KNEW I WORKED IN A FUCKING SCIF.
Stupid ass 90 second timer to get from the phone locker to my desk, sign into a computer still running off a spinning disk, and pray i can get logged into the timecard…
This explains the what but not the why.
Why??
I wasn’t allowed to bring in my phone, which has the authenticator app. And I had to log in on a provided device. And I use 2FA.
The guy didn’t even seem surprised when I asked him for current time to look up the current code, so probably this indeed was within the expectations.
“You can have the password printed out” - part of the instructionsOr they could just give a you a hardware token like Thales does.
But why couldn’t you bring a phone where you were going, and why did you have to log into a strange device?
What were you doing?
High security stuff where anything electronic is a spy device until thoroughly proven otherwise. You’re not going to get a specific answer unless OP is an idiot.
I’m going to brainstorm a few ideas because I’m really curious about this. It sounds like an exciting life to live.
Would these be examples of the following?
- a job interview with a corporate or governmental organization demanding high secrecy where you still have to log into your job portal for some reason.
- you are a consultant on a high security technical project and you are somehow allowed to access the regular internet on a device that’s not your own and use some tools for which you have an account.
These are the only things I can think of. For any regular job, I don’t understand why they wouldn’t just give you a hard token. One of those things that you put on a key ring, which shows you a time-based second factor string of numbers on a little LCD screen.
I had one of those and I was not doing anything sensitive. I was just an environmental educator working for the state government and I had to use it to login to the state laptop to submit my time sheets.
On the other hand, if they won’t give you a hard token, because they’re worried you might bring your own device that looks like a hard token and replicates their hard token except with additional spy hardware, I’m not sure why they are allowing you to log into something on that laptop.
Or if they do expect you to log into something on that laptop, I don’t understand why you’d have to come up with your own custom solution rather than them have some kind of system that everybody uses.
I like the ideas here, so much so that I feel bad for giving you a disappointing answer: exam.
No own electronic devices in the exam room. That included everything, phones, watches, calculators and they also specifically mentioned “hearing aid” while giving out all instructions verbally.
Perhaps if there was someone it applied to they wouldn’t but…
And I had to log into our system to take it, which uses TOTP 2FA. An odd situation. Since the only other thing from clothes being allowed was a pen and paper with password (if needed), here we are.But one real world example I heard from someone is no unapproved devices being brought into the server room.
Sorry, nothing interesting going on in here.
That, uh, defeats the purpose of 2FA? Like completely lol
2fa is something you have and something you know.
Password is something you know, this paper is something you have.
Something you know, this paper will quickly become something everyone knows the minute the weakest link in your company security pipeline gets a hold of one.
Thats why they are time sensitive.
No.
Password I remember is the 1st factor, a valid code from this list (which depends on time) is the second factor.It’s same as using the phone, except that here they were precomputed and on paper for some time span. None of these are valid now (well, maybe there is one, it’s a bunch of number combinations after all), and you don’t have the private key to generate more.
Say, you can tell that at 10:02:30 UTC the valid code was 262887, but you don’t know what it is now.That’s the advantage of TOTP, they expire. If it were plain HOTP, I’d only need 1 code at a time anyway.
It does. If you were to lose this paper while it were active any hacker could access your account. At least your phone has a PIN or pattern they also have to guess. This is just waiting there to be social engineered away from you (if it were still active, which good thing its not)
But they’d also need the password.
Alternative would be disabling 2FA altogether.
I believe most passwords are brute forced or phished nowadays, so unless you have some password manager changing your passwords every hour or so the password is probably pretty moot if the employee has to set it.
Brute-forcing would take some bit of time. If the 6 digit code, 3 combinations of which are likely valid at a time becomes your only factor, you’ve already lost. Long randomly generated combinations are unrealistic to brute-force. For now at least.
And here’s a screenshot from when I brute-forced the 2FA to my Lemmy account because I trusted the wrong app (Cisco Duo and its backups without version control wiping everything after turning on older device):
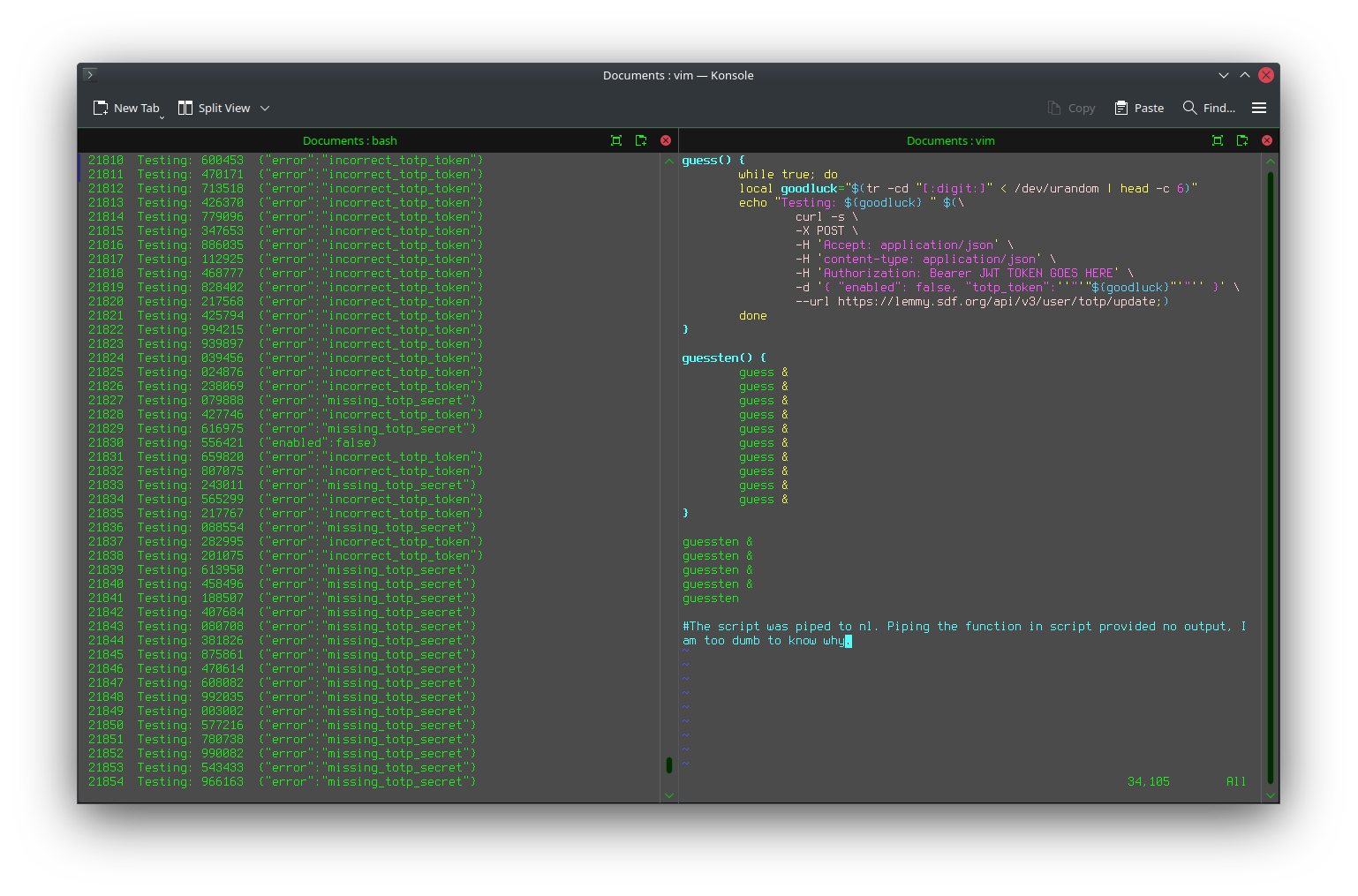 6 digits isn’t much.
6 digits isn’t much.Also I hate how it’s implemented everywhere. We figured out that telling someone whether the password or username is incorrect is a bad thing, so now we do “username or password incorrect”. But what about 2FA? Username is easy to get if targeting a specific person.
If you can get to 2FA, you know the password was correct. That’s the case basically everywhere. Then it’s just 6 digits to guess. And typically you also only get notified about logins when successful. Too late at that point.
My wish would be to take both password and 2FA code at once, and just return “password or 2FA invalid” if one or both of them are wrong.Any sane implementation should rate limit you to 3 tries/min
I wish hardware tokens or something were more prevalent or anything that doesn’t require me to visit 2 separate pages (login then 2fa) to login everytime. All the services I use at work timeout at ~15 minutes and it can be a slog. Software authenticators are convenient to keep track of but theres got to be a better way.
aaaaalmost completely. Knowing a second piece of information technically counts, it’s just like … about as secure as using someone’s SSN for the 2fa, which is absolutely stupid.
about as secure as using someone’s SSN for the 2fa
I’ll give you one better. For a certain thing, the university I attend decided to use birth numbers as a password. And that was the only factor.
Mind you, in Slovakia, the birth number consists of birth date + random 4 digits.
Much safety.Anyway, SSN doesn’t expire in less than 4 hours.
That’s why it’s ‘about’ as stupid. Many US services only really need basic PII to at least set up an account, which is scarily low levels of security.
No? Two separate pieces of information aren’t two factors.
But this would be the factor “ownership” and “knowledge”. Anyone attempting to hack into OP’s account needs both the paper (or a copy thereof) AND the password. Just like withdrawing money from ab ATM requires the card and a PIN.
Though the fact you can easily copy the paper makes it a pretty weak “ownership” factor. Just like how using eye color would be a pretty weak “identity” factor.
You know employees are taping this to their cubicle lol all it would take is some white hat grabbing it off your desk before you all have to do special training from IT
This is different from an employee leaving their 2FA device at their desk how?
Most 2FA is software on someone’s phone, like Microsoft Authenticator. Its not different from leaving a device. It is very different from leaving your phone.
I don’t follow what you’re trying to say here. (The last 2 sentences contradict in my mind)
Anyway, phone vs this tomfoolery, it might not be more/less secure, just different.
What’s on paper is all there will be, as it doesn’t include the secret for generating additional codes.
Phone has that, but also has a screen lock. Whether that is easy to bypass will depend on environment, but after the first unlock, it is at least realistic.
Plus you have people like my father who go by “no lock, nothing to hide”.For immediate exploit, paper looses.
For later persistent exploitation, phone looses.Also, no one’s going to have endless scrolls of codes like this. 2 pages for less than 4 hours. Round that up to 2 hours per page, that would be 12 pages per day, 360 pages per month, 4,380 pages per year.
I had to do this, because it was a requirement (they even recommended to print out the password). Actually, they didn’t mention 2FA, just to print out the password (and no use of personal devices). This is the best I could do given the environment.There are purposed 2FA devices that aren’t your phone. Leaving one of those laying around is about the same security level as leaving these papers is what that says. Either way that sounds like ass to deal with regardless of how secure it is. Give me Aegis or give me death.
Oh, how could I forget that. My bank uses them. But it also needs my (physical) debit card and its PIN.
Bit cumbersome to use.







