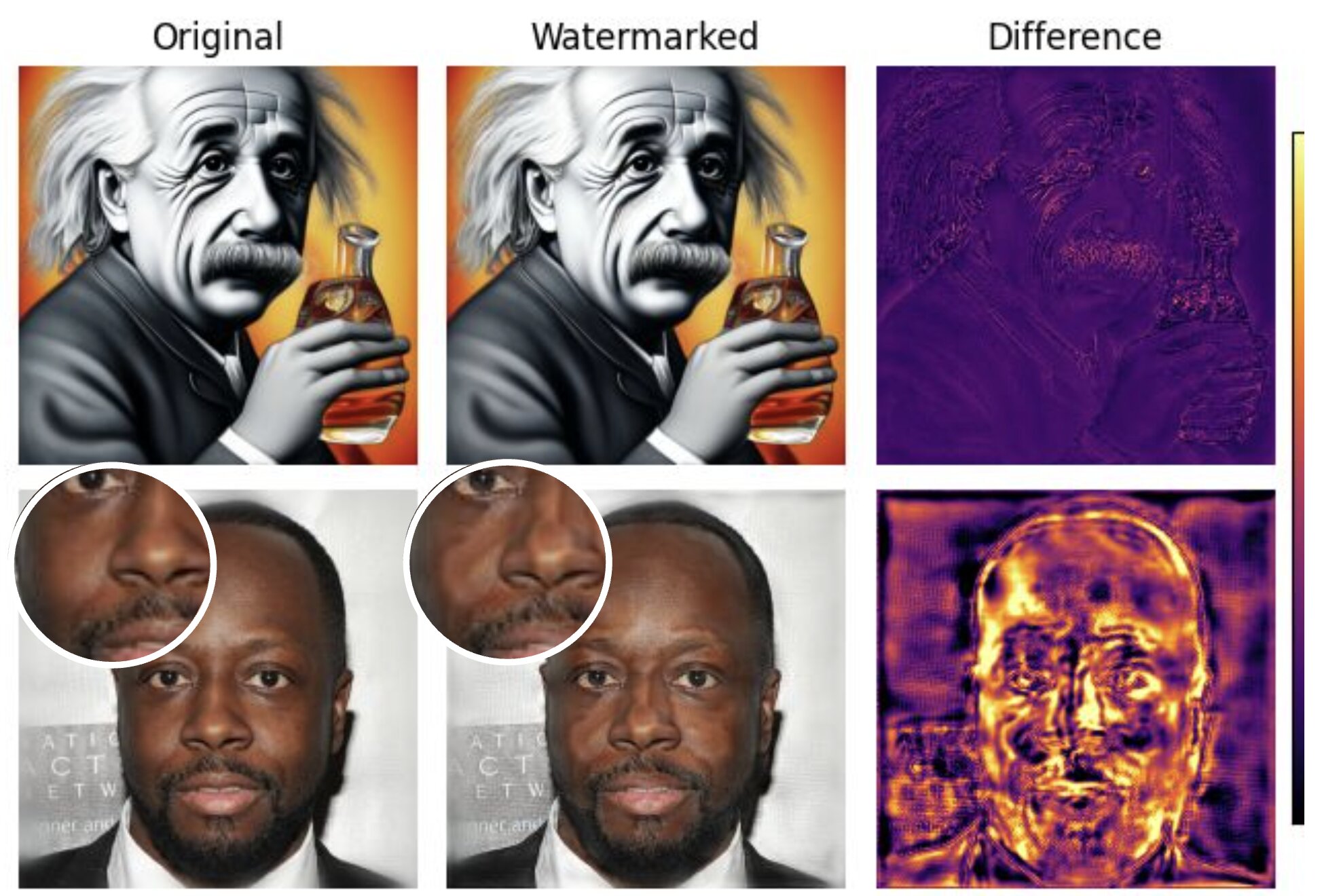
Well, at least we have a study to support the glaringly obvious problems with watermark requirements.
There is a solution, but y’all aren’t going to like it.
The solution is blockchain. Actually, it’s even worse, the solution is NFT’s.
Not the scammy, crypto bro, nonsense it has been used for; but the actual technology.
A cryptographically secure digital token that can track where something was made, where it’s being used, who has the rights to it, and ensures that it’s authentic and not some copy made with AI.
Unfortunately, thanks to crypto bros, the technology has become so tainted by scams that most people get upset just hearing the letters NFT, so adoption isn’t likely.
There are other privacy issues with having an indelible marker as to the origin and chain of custody of every digital artifact. And other non-privacy issues.
So the idea here is that my phone camera attaches a crypro token to the metadata of every photo it takes? (Or worse, embeds it into the image steganographically like printer dots.) Then if I send that photo to a friend in signal, that app attaches a token indicating the transfer? And so on?
If that’s a video of say, police murdering someone, maybe I don’t want a perfect trail pointing back to me just to prove I didnt deep fake it. And if that’s where we are, then every video of power being abused is going to “be fake” because no sane person would sacrifice their privacy, possibly their life, to “prove” a video isnt AI generated.
And those in power, the mainstream media say, aren’t going to demonstrate the crypto chain of custody on every video they show on the news. They’re going to show whatever they want, then say “its legit, trust us!” and most people will.
These are the fundamental issues with crypto that people actually don’t understand: too much of it is actually opt-in, it’s unclear to most people what’s actually proved or protected, and it doesn’t actually address or understsnd where trust, authority, and power actually come from.
I don’t think this is that controversial. If you take out NFTs, it’s using the block chain as a hash. I think that works, but at that point you might as well use regular hashes to verify the integrity of your video
Just fucking sign it. With your private key.
And publish your public key.
Then everyone will be able to verify it’s your work, and no deepfake will ever pass that test.
Yeah, I don’t know why this is so difficult. Can even have players that autoread the signature to tell you the source/etc.
at that point you might as well use regular hashes to verify the integrity of your video
Generated by what authority, though?
math?
Who does the math?
You can have whatever token you want with all the metadata, licensing and ownership information you want…
…unless you plan on only seeing images in your own platform, nobody gives a shit, people will take screenshots and image files and share and use them however they want. There’s no world in which you load a full DRM plugin or do 4 different types of handshake with a full blockchain just to load a jpeg into a comment.
The tech would have been great for bestowing ownership over the digital goods bought with microtransactions, but never would have gotten there since corpos have the rule of law under their thumb.
Sorry for blowing this on you, but fuck blockchain, fuck NFTs.
What we need is better understanding of cryptography.
PGP has solved this problems decades ago, and crypto has just borrowed some parts, but made it worse in every possible way and into incomprehensible depths.
Again, fuck crypto, fuck NFTs.
I should make a guide on how to use GPG.
I thought GPG was bad? I don’t have enough personal experience with it to quickly summarize or opine on the merits of either of these two articles, but:
The PGP Problem: https://www.latacora.com/blog/2019/07/16/the-pgp-problem
What To Use Instead of PGP: https://soatok.blog/2024/11/15/what-to-use-instead-of-pgp/
I do agree with “fuck NFTs” though, and mostly agree with “fuck cryptocurrency” (mostly because porn and drugs are in my view legitimate use cases for at least a hypothetical non-environmentally-destructive cryptocurrency).
It’s not good.
But it’s leagues better than crypto.
I hate typing ‘asymmetric key cryptography’, and GPG is just three letters.
Those blog posts explain a lot, but one use case is missing (at least I don’t see it apart from git commit signing), and that is verifying the source of a public message.
And I do wish we tried using the private keys more. Specially now when anyone can deepfake anything.
If I ever release my nudes, never trust them unless they are signed and you can check them with public key in my profile.
I think maybe an update to the image format standards, where it like somehow includes a hash of the instrument that has taken the photo and video, and thus, only such media that can be verified to have been taken by a physical instrument can be used in like legal matters, or reporting or journals.
Either this hash can be verified by some algorithm, or maybe the media could depend on this hash in such a way that the media is corrupted if it gets altered.
There are already plans for metadata signing. I think some high end Canon cameras might do it already. It basically allows proof (via public private key of the hash) that a particular camera took that photo.
The idea is that you can create a chain of custody with an image. Each edit requires a new signature, with each party responsible for verifying the previous chain, to protect their own reputation.
It’s far from perfect, but will help a lot with things like legal cases.
The obvious limitation being that you can take a real photo with attestation with a real camera of a real computer screen displaying any fake shit you can imagine, then you have an officially hashed photo of anything.
If you’ve ever tried this, the moire pattern of pixels is obvious. You’d need a much higher resolution display than image sensor.
So you want to EMB make, model and SN into images now? Metadata on crack
If the hash can be created at the time the inage/media is created then it can be faked.
Depends on the hash - some are tracable to a crypotographic public key and thus cannot be faked. Most are not but there are options that can be. Normally we refer to such things as signed not a hash but same thing to the layman who doesn’t understand this.
In order for it to be traceable with a public key, it needs to be signed with the private key. That means the private key has to be on the camera. That means it can be extracted from the camera and leaked.
Maybe. There are ways to assign a private key that is not easy to extract. a chip that creates a private key on first poweron and then saves to internal memory for example.
Not easy to extract sure, but is it secure enough for you to claim that it hasnt been leaked and so forms a secure chain of custody? Once one has been leaked then that can be used to sign any fake pictures you like. I woudnt buy that for anything for serious than is this meme picture real.
There are ways to be sure of authenticity, ways that can’t be faked.
So we should all have to throw away or phones, cameras, etc. And buy new ones that have proprietary hardware attestation?
Oh come on, you’re gonna do that in two years anyway.
No <3
Are we gonna have to start using let’s encrypt as part of photography?!
Leica, Sony, Nikon, and Canon have backed an Adobe-created digital signature solution for authentication of photos directly in the camera, including metadata like time/date stamps. But that’s mainly for journalism and professional grade cameras, not the cell phones that 90+% of new images are created on.
This is not surprising because AI mimics plausible patterns in images, watermarks are mostly made with noise
By the authority of God bitch idk